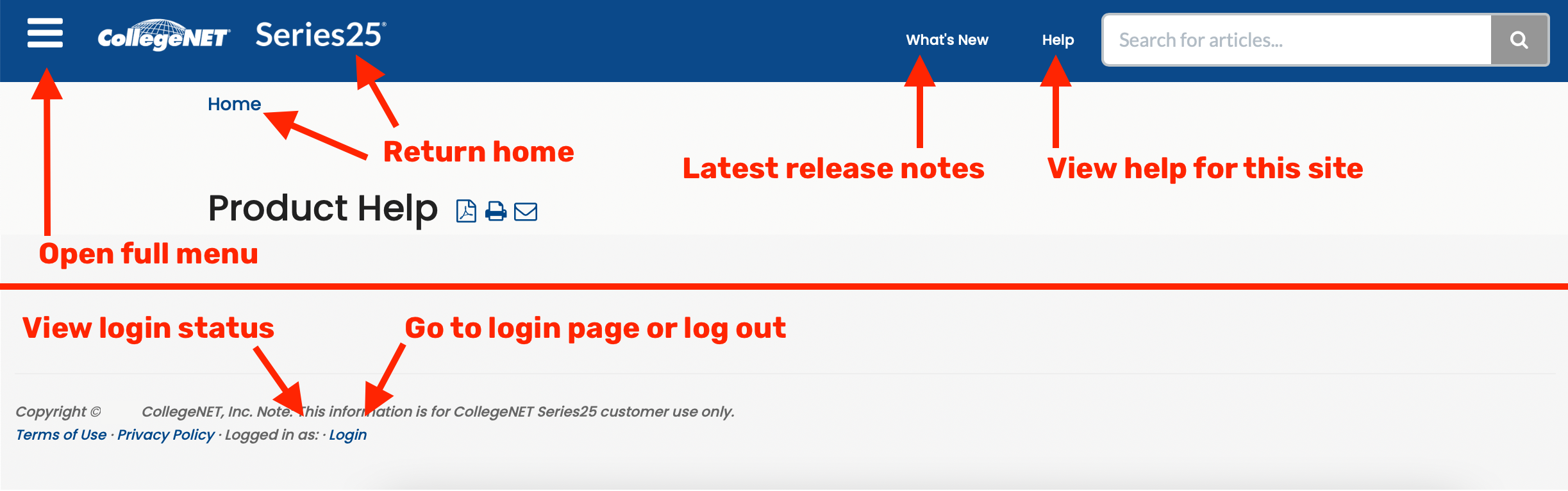
This Page Requires a Log In
Log In or Come Back Through a Series25 Application
Please enter your log in credentials below. Contact Technical Support if you don't already have credentials, or use a help link when logged in to a Series25 application.
If you're coming from an application and not expecting a login, your session may have expired. Please return to your Series25 application to log in again.
Not authorized. Log in below to access article.
Login